workflow New-Tenant {
param([object]$resourceObject)
# write-output ($resourceObject.Name -split "_" | select -first 1)
# Get Connection Credentials. Change Name to your own Asset.
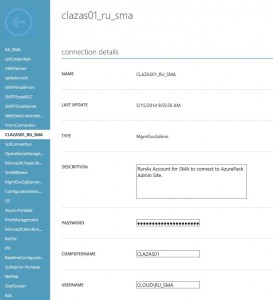
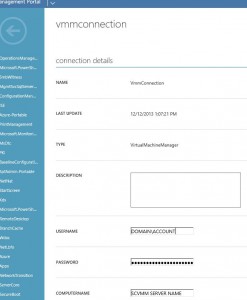
$con = Get-AutomationConnection -Name 'CLAZAS01_RU_SMA'
$secpasswd = ConvertTo-SecureString $con.Password -AsPlainText -Force
$ruSMAcreds = New-Object System.Management.Automation.PSCredential ($con.username, $secpasswd)
# Execute commands on AzurePack Admin site. Connect with Asset Credentials
InlineScript {
$con=$USING:Con
$ruSMAcreds=$USING:ruSMAcreds
$resourceObject=$USING:resourceObject
Invoke-Command -ComputerName $con.computername -Credential $ruSMAcreds -ArgumentList ($resourceObject.Name -split "_" | select -first 1),$con -ScriptBlock {
param(
$NewUserEmail,
$con
)
# We use ADFS for our Azure Pack site, so have to generate a ADFS Token first.
function Get-AdfsToken([string]$adfsAddress, [PSCredential]$credential)
{
$clientRealm = 'http://azureservices/AdminSite'
$allowSelfSignCertificates = $true
Add-Type -AssemblyName 'System.ServiceModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'
Add-Type -AssemblyName 'System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'
$identityProviderEndpoint = New-Object -TypeName System.ServiceModel.EndpointAddress -ArgumentList ($adfsAddress + '/adfs/services/trust/13/usernamemixed')
$identityProviderBinding = New-Object -TypeName System.ServiceModel.WS2007HttpBinding -ArgumentList ([System.ServiceModel.SecurityMode]::TransportWithMessageCredential)
$identityProviderBinding.Security.Message.EstablishSecurityContext = $false
$identityProviderBinding.Security.Message.ClientCredentialType = 'UserName'
$identityProviderBinding.Security.Transport.ClientCredentialType = 'None'
$trustChannelFactory = New-Object -TypeName System.ServiceModel.Security.WSTrustChannelFactory -ArgumentList $identityProviderBinding, $identityProviderEndpoint
$trustChannelFactory.TrustVersion = [System.ServiceModel.Security.TrustVersion]::WSTrust13
if ($allowSelfSignCertificates)
{
$certificateAuthentication = New-Object -TypeName System.ServiceModel.Security.X509ServiceCertificateAuthentication
$certificateAuthentication.CertificateValidationMode = 'None'
$trustChannelFactory.Credentials.ServiceCertificate.SslCertificateAuthentication = $certificateAuthentication
}
$ptr = [System.Runtime.InteropServices.Marshal]::SecureStringToCoTaskMemUnicode($credential.Password)
$password = [System.Runtime.InteropServices.Marshal]::PtrToStringUni($ptr)
[System.Runtime.InteropServices.Marshal]::ZeroFreeCoTaskMemUnicode($ptr)
$trustChannelFactory.Credentials.SupportInteractive = $false
$trustChannelFactory.Credentials.UserName.UserName = $credential.UserName
$trustChannelFactory.Credentials.UserName.Password = $password #$credential.Password
$rst = New-Object -TypeName System.IdentityModel.Protocols.WSTrust.RequestSecurityToken -ArgumentList ([System.IdentityModel.Protocols.WSTrust.RequestTypes]::Issue)
$rst.AppliesTo = New-Object -TypeName System.IdentityModel.Protocols.WSTrust.EndpointReference -ArgumentList $clientRealm
$rst.TokenType = 'urn:ietf:params:oauth:token-type:jwt'
$rst.KeyType = [System.IdentityModel.Protocols.WSTrust.KeyTypes]::Bearer
$rstr = New-Object -TypeName System.IdentityModel.Protocols.WSTrust.RequestSecurityTokenResponse
$channel = $trustChannelFactory.CreateChannel()
$token = $channel.Issue($rst, [ref] $rstr)
$tokenString = ([System.IdentityModel.Tokens.GenericXmlSecurityToken]$token).TokenXml.InnerText;
$result = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($tokenString))
return $result
}
# Fill in values for your environment.
# ADFS Server address
$adfsAddress = 'https://adfs.labcenteronline.com'
$credentials=$ruSMAcred
# Name and port for the Admin Site.
$adminUri = 'https://adminsite.labcenteronline.com:30004'
$secpasswd = ConvertTo-SecureString $con.Password -AsPlainText -Force
$ruSMAcreds = New-Object System.Management.Automation.PSCredential ($con.username, $secpasswd)
$token = Get-AdfsToken -adfsAddress https://adfs.labcenteronline.com -credential $ruSMAcreds
$newuser = Get-MgmtSvcUser -Token $token -AdminUri $adminUri -DisableCertificateValidation -Name $NewUserEmail
$uname=$newuser.name
# Change the e-mail suffix to match your environment.
if (($uname -like "*@truesec.com") -or ($uname -like "*@truesec.se")) {
#TrueSec Employees
# Replace DisplayName to match your Plan.
$plan = Get-MgmtSvcPlan -Token $token -AdminUri $adminUri -DisableCertificateValidation -DisplayName "*Tenan*Truesec*" | where State -notlike "Decommissioned" | select -first 1
$planname=$plan.DisplayName
# Get Current Subscriptions for user that matches the Plan to get added to.
$currentsubs = Get-MgmtSvcSubscription -Token $token -AdminUri $adminUri -DisableCertificateValidation | where AccountAdminLiveEmailId -like "$uname" | where OfferFriendlyName -like "$planname"
if ($currentsubs.count -lt $plan.MaxSubscriptionsPerAccount){
$newsubscription = Add-MgmtSvcSubscription -Token $token -AdminUri $adminUri -DisableCertificateValidation -AccountAdminLiveEmailId $uname -AccountAdminLivePuid $uname -PlanId $plan.id -FriendlyName $plan.DisplayName
write-output "$uname has been added to $planname with subscriptionid $newsubscription"
}
else {
Write-Output "User already has a subscriptions for $planname"
}
}
else {
write-output "Not a Truesec Employee, did not add user to any plan."
}
}
}
}